[导读]:直到前两天单位又有电脑中永恒之蓝勒索病毒,才意识到这个病毒或者说这一类病毒并不是说过去了就过去了,而是一直存在的。而且单位内部电脑中了此病毒之后更加麻烦,因...
直到前两天单位又有电脑中永恒之蓝勒索病毒,才意识到这个病毒或者说这一类病毒并不是说过去了就过去了,而是一直存在的。而且单位内部电脑中了此病毒之后更加麻烦,因为它会向局域网其它电脑进行扩散传播。所以我们网管员第一时间在交换机上关机了445端口,以防止其感染其它未打补丁的电脑。但是这样一来,好多办公室都出现了打印机无法共享的现象。
WannaCry 勒索软件一旦中招之后会加密硬盘文件,无法恢复,因为它的加密算法是不可逆的,除非你支付相关的赎金,所以说危害很严重,一定要引起重视。针对此病毒,我们可以做的:
一、终端电脑立即打上 MS17-010 漏洞补丁。
二、外部的网络设备上(路由器、防火墙、IPS等)屏蔽445端口。
绿盟科技是国内著名的网络安全厂商,在我读大学那会已经很有名气了,他们出了一个勒索病毒安全加固工具V1.4,是 BAT 程序,下载下来之后看了源代码。它的“加固”方式主要是两点:一是关闭了 Server 服务,二是通过防火墙屏蔽了445端口。程序适用于 Windows 7/10/ 和 Windows Server 2003/2008/2012/2016,使用方便,特此推荐,代码如下。
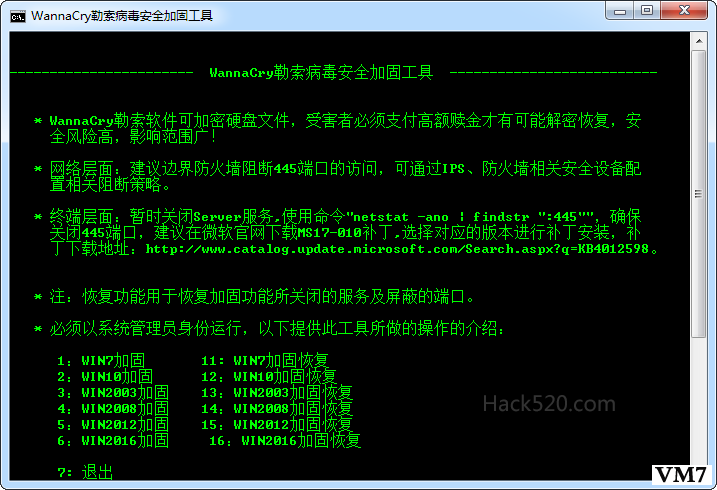
@echo off mode con: cols=85 lines=40 :NSFOCUSXA title WannaCry勒索病毒安全加固工具 color 0A cls echo. echo. echo ----------------------- WannaCry勒索病毒安全加固工具 -------------------------- echo. echo. echo * WannaCry勒索软件可加密硬盘文件,受害者必须支付高额赎金才有可能解密恢复,安 echo 全风险高,影响范围广! echo. echo * 网络层面:建议边界防火墙阻断445端口的访问,可通过IPS、防火墙相关安全设备配 echo 置相关阻断策略。 echo. echo * 终端层面:暂时关闭Server服务,使用命令"netstat -ano | findstr ":445"",确保 echo 关闭445端口,建议在微软官网下载MS17-010补丁,选择对应的版本进行补丁安装,补 echo 丁下载地址:https://www.hack520.com/513.html。 echo. echo * 注:恢复功能用于恢复加固功能所关闭的服务及屏蔽的端口。 echo. echo * 必须以系统管理员身份运行,以下提供此工具所做的操作的介绍: echo. echo 1:WIN7加固 11: WIN7加固恢复 echo 2:WIN10加固 12:WIN10加固恢复 echo 3:WIN2003加固 13:WIN2003加固恢复 echo 4:WIN2008加固 14:WIN2008加固恢复 echo 5:WIN2012加固 15:WIN2012加固恢复 echo 6:WIN2016加固 16:WIN2016加固恢复 echo. echo 7: 退出 echo 绿盟科技 V1.4 echo www.nsfocus.com echo echo --------------------------------------------------------------------------------- echo. set start= set /p start= 输入(1 2 3 4 5 6)后按回车键: if "%start%"=="1" goto WIN7 if "%start%"=="2" goto WIN10 if "%start%"=="3" goto WIN2003 if "%start%"=="4" goto WIN2008 if "%start%"=="5" goto WIN2012 if "%start%"=="6" goto WIN2016 if "%start%"=="11" goto WIN7X if "%start%"=="12" goto WIN10X if "%start%"=="13" goto WIN2003X if "%start%"=="14" goto WIN2008X if "%start%"=="15" goto WIN2012X if "%start%"=="16" goto WIN2016X if "%start%"=="7" goto quit goto NSFOCUSXA :WIN7 net stop server /Y > nul sc config lanmanserver start= disabled netsh advfirewall set currentprofile state on > nul netsh advfirewall firewall add rule name="DenyEquationTCP" dir=in action=block localport=445 remoteip=any protocol=tcp > nul netsh advfirewall firewall add rule name="DenyEquationUDP" dir=in action=block localport=445 remoteip=any protocol=udp > nul echo --------------------------------------------------------------------------------- echo * Windows 7系统加固命令执行完毕! echo . pause goto NSFOCUSXA :WIN10 net stop server > nul sc config lanmanserver start= disabled netsh firewall set opmode enable > nul netsh advfirewall firewall add rule name="DenyEquationTCP" dir=in action=block localport=445 remoteip=any protocol=tcp > nul netsh advfirewall firewall add rule name="DenyEquationUDP" dir=in action=block localport=445 remoteip=any protocol=udp > nul echo --------------------------------------------------------------------------------- echo * Windows 10系统加固命令执行完毕! echo . pause goto NSFOCUSXA :WIN2003 net stop server > nul net start sharedaccess > nul sc config lanmanserver start= disabled netsh firewall add portopening protocol = ALL port = 445 name = DenyEquationTCP mode = DISABLE scope = ALL profile = ALL > nul echo --------------------------------------------------------------------------------- echo * Windows Server 2003系统加固命令执行完毕! echo . pause goto NSFOCUSXA :WIN2008 net stop server /Y > nul sc config lanmanserver start= disabled netsh advfirewall set currentprofile state on > nul netsh advfirewall firewall add rule name="DenyEquationTCP" dir=in action=block localport=445 remoteip=any protocol=tcp > nul netsh advfirewall firewall add rule name="DenyEquationUDP" dir=in action=block localport=445 remoteip=any protocol=udp > nul echo --------------------------------------------------------------------------------- echo * Windows Server 2008系统加固命令执行完毕! echo . pause goto NSFOCUSXA :WIN2012 net stop server > nul net start MpsSvc > nul sc config lanmanserver start= disabled netsh advfirewall firewall add rule name="DenyEquationTCP" dir=in action=block localport=445 remoteip=any protocol=tcp > nul netsh advfirewall firewall add rule name="DenyEquationUDP" dir=in action=block localport=445 remoteip=any protocol=udp > nul echo --------------------------------------------------------------------------------- echo * Windows Server 2012系统加固命令执行完毕! echo . pause goto NSFOCUSXA :WIN2016 net stop server > nul sc config lanmanserver start= disabled netsh advfirewall firewall add rule name="DenyEquationTCP" dir=in action=block localport=445 remoteip=any protocol=tcp > nul netsh advfirewall firewall add rule name="DenyEquationUDP" dir=in action=block localport=445 remoteip=any protocol=udp > nul echo --------------------------------------------------------------------------------- echo * Windows Server 2016系统加固命令执行完毕! echo . pause goto NSFOCUSXA :WIN7X net start server /Y > nul sc config lanmanserver start= auto netsh advfirewall set currentprofile state on > nul netsh advfirewall firewall delete rule name="DenyEquationTCP" > nul netsh advfirewall firewall delete rule name="DenyEquationUDP" > nul echo --------------------------------------------------------------------------------- echo * Windows 7系统加固恢复命令执行完毕! echo . pause goto NSFOCUSXA :WIN10X net start server > nul sc config lanmanserver start= auto netsh firewall set opmode enable > nul netsh advfirewall firewall delete rule name="DenyEquationTCP" > nul netsh advfirewall firewall delete rule name="DenyEquationUDP" > nul echo --------------------------------------------------------------------------------- echo * Windows 10系统加固恢复命令执行完毕! echo . pause goto NSFOCUSXA :WIN2003X net start server > nul net start sharedaccess > nul sc config lanmanserver start= auto netsh firewall delete portopening protocol = TCP port = 445 > nul netsh firewall delete portopening protocol = UDP port = 445 > nul echo --------------------------------------------------------------------------------- echo * Windows Server 2003系统加固恢复命令执行完毕! echo . pause goto NSFOCUSXA :WIN2008X net start server /Y > nul sc config lanmanserver start= auto netsh advfirewall set currentprofile state on > nul netsh advfirewall firewall delete rule name="DenyEquationTCP" > nul netsh advfirewall firewall delete rule name="DenyEquationUDP" > nul echo --------------------------------------------------------------------------------- echo * Windows Server 2008系统加固恢复命令执行完毕! echo . pause goto NSFOCUSXA :WIN2012X net start server > nul net start MpsSvc > nul sc config lanmanserver start= auto netsh advfirewall firewall delete rule name="DenyEquationTCP" > nul netsh advfirewall firewall delete rule name="DenyEquationUDP" > nul echo --------------------------------------------------------------------------------- echo * Windows Server 2012系统加固恢复命令执行完毕! echo . pause goto NSFOCUSXA :WIN2016X net start server > nul sc config lanmanserver start= auto netsh advfirewall firewall delete rule name="DenyEquationTCP" > nul netsh advfirewall firewall delete rule name="DenyEquationUDP" > nul echo --------------------------------------------------------------------------------- echo * Windows Server 2016系统加固恢复命令执行完毕! echo . pause goto NSFOCUSXA
点击下载勒索病毒安全加固工具 1.4 最新版
本文来自投稿,不代表微盟圈立场,如若转载,请注明出处:https://www.vm7.com/a/jc/7924.html


